NIST SP 800-171 Overview
The National Institute of Standards and Technology (NIST) developed Special Publication (SP) 800-171 ("Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations"), which outlines security standards for the protection of sensitive information. The publication "provides recommended security requirements for protecting the confidentiality of Controlled Unclassified Information (CUI) when the information is resident in nonfederal systems and organizations. […] The requirements apply to all components of nonfederal systems and organizations that process, store, and/or transmit CUI, or that provide protection for such components." Since the initial release, the requirements outlined in SP 800-171 have increasingly been included in government contracts for which the Department of Defense (DoD) is the funding source, and the requirements might soon be applied to other government contracts. Colleges and universities that are contractors or subcontractors for these contracts must be in compliance with SP 800-171. Assessment of that compliance will be handled through processes specified by the Cybersecurity Maturity Model Certification (CMMC) program.
This overview provides:
- A review of the timeline that introduced NIST SP 800-171 "Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations" as a compliance framework
- An overview of the control families for the 110 controls
- A discussion of the impacts and concerns for higher education
Timeline: From DFARS 252.204-7012 to CMMC 2.0
Below are some of the key milestones in the evolution from the introduction of the Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012 ("Safeguarding Covered Defense Information and Cyber Incident Reporting") in 2015 to the announcement of the CMMC 2.0 program in 2022. Institutions with DoD contracts have likely been working for several years on becoming compliant. It should be noted that at present, the CMMC program only applies to DoD-funded research initiatives, but the NIST SP 800-171 standard is being considered for adoption by other groups in the federal government.
2015: DFARS 252.204-7012 introduces NIST SP 800-171 as the compliance standard for nonfederal systems.
2018: SP 800-171A is released.
2020: CMMC 1.0, which included five maturity levels, is released (January 31, 2020).
2020: DFARS 7012 Interim Rule for DoD is released (November 29, 2020). Some contracts appear that require Supplier Performance Risk System (SPRS) entry.
2020: Dept. of Education "Protecting Student Information – Compliance with CUI and GLBA" is released.
2022: CMMC 2.0 for DoD, is released. CMMC 2.0 reduces the five maturity levels of CMMC 1.0 to three levels, eliminating levels 2 and 4. CMMC 2.0 removes the maturity measures that were part of CMMC 1.0 and returns it to being based solely on NIST SP 800-171.
Definitions of the Control Families
NIST SP 800-171, a subset of NIST SP 800-53 ("Security and Privacy Controls for Information Systems and Organizations"), is used to demonstrate compliance with DFARS 252.204-7012 ("Safeguarding Covered Defense Information and Cyber Incident Reporting") for handling Controlled Unclassified Information (CUI). NIST 800-171 outlines 14 control families, covering 110 separate controls (source: Overview of NIST SP 800-171 Requirements | RSI Security):
- Access Control: Comprising 22 requirements (2 basic, 19 derived) governing ways in which access to Covered Defense Information (CDI), CUI, and other protected information is granted and restricted
- Awareness and Training: Comprising 3 requirements (2 basic, 1 derived) governing how often regular and special training activities occur and what content they must cover
- Audit and Accountability: Comprising 9 requirements (2 basic, 7 derived) for regular external auditing, logging, and protection of audit information for accountability
- Configuration Management: Comprising 9 requirements (2 basic, 7 derived) related to specific settings and configurations for software and hardware, beyond their defaults
- Identification and Authentication: Comprising 11 requirements (2 basic, 9 derived) governing user passwords, multifactor authentication (MFA), and other credentials
- Incident Response: Comprising 3 requirements (2 basic, 1 derived) governing a company's programmatic response to identified hacks, breaches, and other events
- Maintenance: Comprising 6 requirements (2 basic, 4 derived) specifying schedules for regular, routine maintenance and protocols for special, reparative procedures
- Media Protection: Comprising 9 requirements (3 basic, 6 derived) governing the minimum safeguards for media and servers directly connected to CDI, CUI, etc.
- Personnel Security: Comprising 2 requirements (both basic) governing screening, onboarding, and ongoing security monitoring of personnel to combat insider threats
- Physical Protection: Comprising 6 requirements (2 basic, 4 derived) specifying physical, proximity-based safeguards for hardware related to CDI, CUI, etc.
- Risk Assessment: Comprising 3 requirements (1 basic, 2 derived) governing the programmatic approach to monitoring for, analyzing, and mitigating security risks
- Security Assessment: Comprising 4 requirements (all basic) specifying protocols for routine or special company-wide assessments and corrective measures
- System and Communications Protection: Comprising 16 requirements (2 basic, 14 derived) governing minimum protections for communication networks and systems
- System and Information Integrity: Comprising 7 requirements (3 basic, 4 derived) for swiftly identifying and correcting gaps or flaws in cybersecurity infrastructure
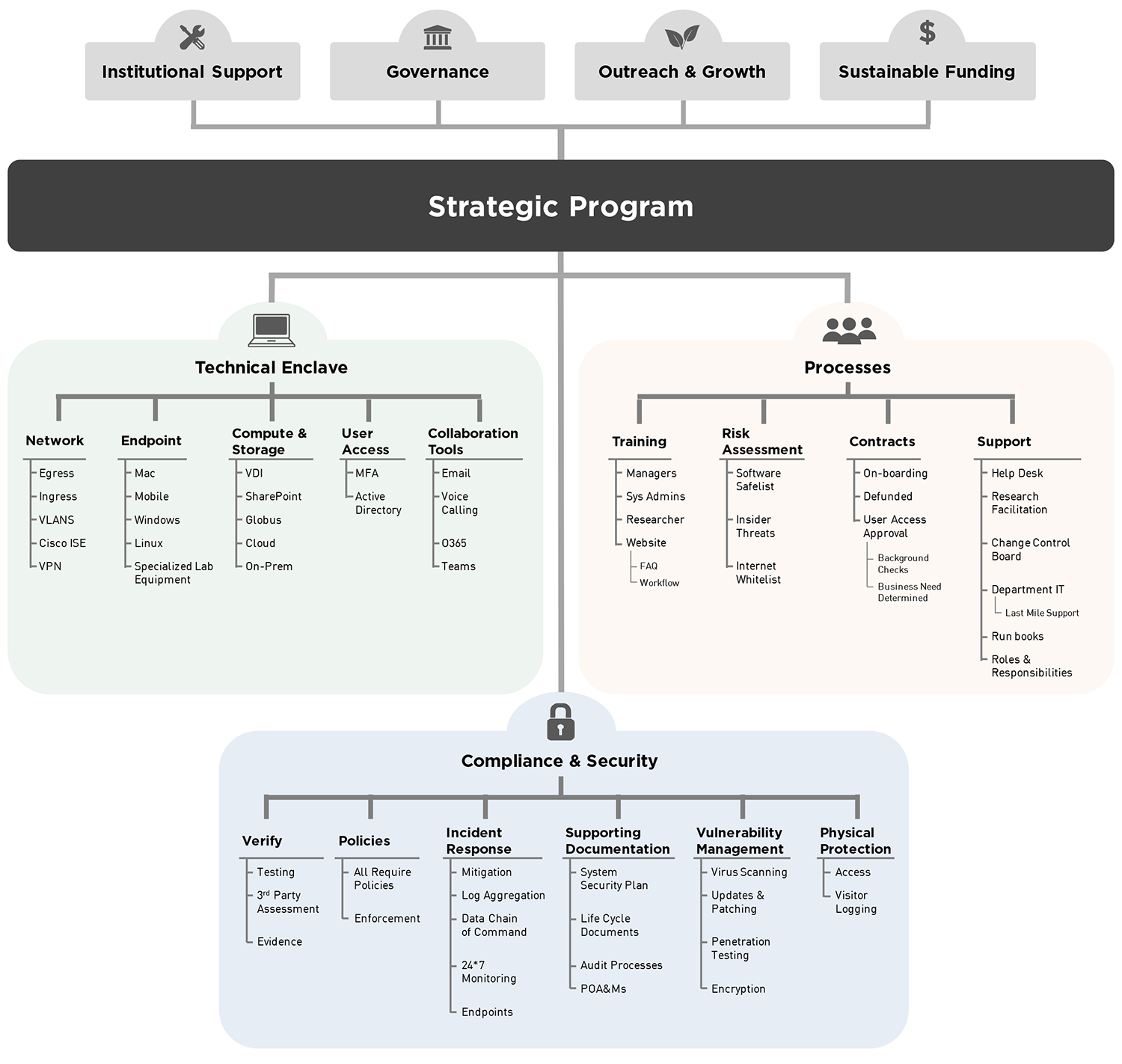
The specifics of each enclave or program will be unique to the institution. Figure 1 illustrates many of the items that may get scoped into or out of the enclave. Every institution will need to define the three major components—technical enclave, compliance and security, and processes—with specifics driven by the project's needs. Additionally, no program can sustain its supported projects without first establishing the following:
- Institutional support for associated contracts (is it part of the research portfolio or not?)
- Governance or some process for how decisions are made
- Outreach and growth so that the project doesn't become a single-use effort
- Sustainable funding so that the enclave remains compliant and available
Impact and Concerns for Higher Education
- Two areas of immediate impact are research and Gramm-Leach-Bliley Act (GLBA) compliance for the Department of Education (ED).
- Research with DoD either directly or indirectly as subcontractors
- DFARS 252.204-7012 is enforced on new contracts, and existing contracts can be amended to include this clause.
- When CMMC is finalized, including implementation timelines, this will require:
- Full compliance with CMMC at proposal submission
- Regular CMMC certification at a frequency yet to be announced
- This impacts subcontract work with other institutions. Colleges and universities are responsible for verifying that their subcontractors are compliant if they will be handling CUI.
- Non-DoD research
- Contracts outside DoD are starting to reference the NIST SP 800-171 standard in their compliance requirements. For now, it's not clear if they will require 100% compliance from the start or allow a minimum threshold with POAMs.
- ED/GLBA compliance
- ED's administration of federal student aid programs is authorized under Title IV of the Higher Education Act of 1965.
- An assessment model has not been announced.
- What part of the student record will be considered CUI is not yet defined.
- It is unknown if the implementation of the framework will differ from the DoD all-or-nothing model imposed by CMMC.
- Research with DoD either directly or indirectly as subcontractors
- Other considerations and impacts
- These initiatives require additional cost, resource time, and ongoing effort to maintain.
- Tracking who needs to be verified as compliant requires constant monitoring. For example, graduate student churn on research projects is a reality.
- Training: Specific, focused training for CUI is not currently available from any of the commercial off-the-shelf vendors. What is available is mentioned elsewhere in this toolkit.
- PI/Researcher Experience
- Some colleges and universities have proposed that affected users have accounts in two separate environments; this could be two email addresses.
- Having to track compliance for training and background screening adds an additional layer of management for moving users on and off of projects.
- Impacts of a project that has CUI:
- Longer lead times to prepare for project start
- Additional costs for access to CUI compliant environments
- Inability to use certain resources like personally owned devices
- Provides higher education institutions a common framework along with CMMC 2.0 on maturing cybersecurity
- Becomes one more framework universities are having to address
- Documentation is needed, and artifacts must be collected, managed, and monitored often using a system designed to track governance, risk, and compliance (GRC). The needs exceed the capabilities of a spreadsheet.
- Scoping
- Scoping guidance and other relevant information can be found at "CMMC Documentation."
- Key infrastructure systems may now require compliance. What are the "connected systems" in your organization? Consider, for example, Splunk, Microsoft Active Directory (AD), vulnerability tools, endpoint detection and response (EDR)—any centrally managed resource that interacts with your CUI environment(s).
- Full compliance with NIST SP 800-171 does not align well with the open nature of the research in a higher education environment.
- The requirements of the physical controls often go against the design of open, collaborative environments that many campuses have strived to create.
- Costly laboratory instruments often have shared access for a number of campus groups, and the expectations and needs of those groups may be at odds with the compliance requirements.
- Vendor impact
- This will require vetting of cloud-based solutions for compliance. For cloud-based solutions you must have a means of evaluating the shared controls in a Microsoft Azure / Amazon Web Services (AWS) / Google Cloud Platform (GCP) environment.
- Third, fourth, or fifth parties—how far down do you need to go to ensure that compliance is being met?
- For research, FedRAMP is an assurance resource.
- For student records, there is no current certification or other assurance documentation at this time.
- Some third-party groups might provide additional information that can be used in your compliance assessment process.
© EDUCAUSE 2022